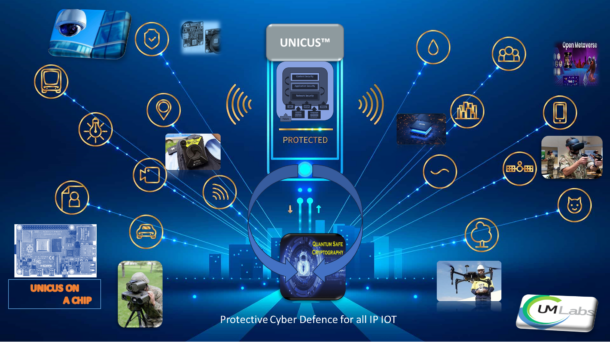
UM-Labs are set up to deliver advanced creative and innovative technology with new designs and developments that have been thoroughly researched and are for the much-needed security solutions across all IP networks, IP applications and IP content/media traffic. This licensable technology can be used to create overlay services or embedded in EDGE IOT devices on a chip, these capabilities through this innovation and research are developed by UM-Labs scientists (across territories inclusive of HQ UK, war zone Ukraine, Czech Republic) now working ever closer with the defence industry to achieve a faster pull-through of next-generation cyber PIA (protect, intercept, archive) policy and build by design capabilities.
Unicus™ from the UM-Labs R&D group solves the Cyber Security issues across all real-time IP network, applications protecting both management traffic as well as content/media. The design is based on IP standards and is extensible to incorporate new intelligent plug-in modules for new protocols and applications running on IP networks. Unicus run as a native service on any cloud platform with deployment at both CORE and EDGE to protect all IOT devices. Unicus RTC, SVSS and IOT are the technology components that enables the fog of cloud by extending protection from the core to remote network edge devices. Unicus protects data in transit by encrypting all traffic and using Quantum Safe algorithms to secure against future threats. Unicus Edge protection is available as a tool kit for system on a chip turn-key solution, as a service or as and embedded product implementation.
Unicus UOS
Unicus UOS is the common operating system and development platform for all Unicus solutions. UOS provides a hardened operating system optimised for protecting and securing real-time communications applications based on standard protocols, on any IP network. UOS provides fully integrated, layered security controls to protect against network threats and to secure real-time services at the application and content level. Feedback between the layers maximises the efficiency and effectiveness of threat responses.
UOS ensures that applications are protected by validating and authenticating all requests, defending against attacks and protecting content with encryption including PQC algorithms guarding against the future threat posed by quantum computers.
Unicus RTC
Unicus RTC secures real-time communication services running SIP, the Session Initiation Protocol. This includes voice and video calls, Instant Messaging and Presence. Unicus RTC is deployed in multiple government and defence locations protecting SIP trunk connections to national Communication Service Providers (CSP), providing protected links to trusted 3rd parties and delivering secure remote communication over any IP network. These deployments have enabled both end-user organisations and CSPs to deliver integrated user services for fixed and mobile voice and video services at security levels up to secret. For these deployments Unicus RTC provides policy controls to manage information flow between security levels.
Unicus SVSS
Unicus SVSS (Streaming Video Security Service) secures video streams from static and mobile cameras. Unicus SVSS was developed with support from DASA and Dstl. Unicus SVSS builds on the UOS architecture to implement Core and Edge devices. Edge devices run on small scale Intel or Arm processors and work with a Unicus SVSS Core to protect video and audio streams. Unicus SVSS is used to secure data streams from body-worn cameras and surveillance cameras including drone mounted cameras.
Unicus® CXR
Unicus CXR uses the same Core/Edge architecture as Unicus SVSS but incorporates additional features to support virtual and augmented reality applications. Unicus secures Cloud eXtended Reality where a cloud rendered scene is overlaid on a view of the local environment, plus other forms of VR and AR. Unicus CXR has been deployed to protect a CXR application based on Nvidia’s Omniverse SDK and running on BT’s 5G network by adding additional security features, authentication and encryption.
Unicus® IoT
Unicus IoT builds on the Core/Edge architecture to secure IoT applications. In common with other Unicus products, Unicus IoT provides protection for both core services and edge devices (sensors and actuators) and secures data flow between edge and core with authentication and encryption including PQC.
SNITCH
SNITCH is a threat intelligence service operated by UM Labs to collate information on active network threats. SNITCH gathers data from honeypots designed to monitor network attacks and from active Unicus platforms. The SNITCH data base currently holds 6 billion attack reports, with constant growth as new repots are added. The SNITCH data is processed using UM Labs’ Large Event Model to provide an AI threat summary to enable Unicus platforms to detect and block new threats.
