The Fortinet and BT relationship is a rapidly expanding and profitable one for both parties, with joint revenues more than doubling over the last 12 months. Together we are building and selling leading edge solutions, such as ‘Secure SD-WAN’, together with BT Enterprise and BT Global into several highly prestigious blue-chip clients. BT also has the highest Fortinet accreditation available and one of only two partners globally to have achieved this. This engagement has also underpinned several ‘internal BT’ deployments for Fortinet and we hope to extend out this particular side of the relationship whilst meeting a number of BT’s strategic objectives around Cloud adoption, Sustainability, Cost reduction and improving Security Posture.
Dave Feeney – BT Account Director
Dave has been in the IT and Cyber security space for over 20 years working for startup organizations like Brightmail and Webroute in the early noughties. This was followed up by an 8-year stint at Symantec and then nearly 6 years at Check point before joining Fortinet in 2021. These last three roles are highlighted by a distinct focus on account management and development into the UK’s largest Telco Operators.
“Working in this sector and focusing on a Telco operator is both diverse and very challenging, but also very rewarding. Telco operators have responsibility for core national infrastructure whilst also constantly evolving and adapting to new customer and market nuances. BT remains a dominant Telco Service Provider with recognizable brands and a great track record of delivery in UK markets and abroad. I am heavily focused on trying to deliver high value, sustainable, cost-effective security solutions that support business growth and change, whether that is in Physical devices, private cloud, public cloud or added value services.
Email: dfeeney@fortinet.com
Andrew Crampton – BT Senior SE
Andrew has been working in the Networking and Cybersecurity arena for 25 years, initially in New Zealand with a home grown router vendor that was eventually acquired by Allied Telesis– through out this period time was spent in South East Asia and China working with a variety of PTTs. Eventually moving to the UK and working as a presales consultant for AT&T, Equant and Interoute (now GTT) with a strong Cisco background.
Andrew spent 10 years with Juniper Networks working in the Service Provider team as a Senior Systems Engineer, consulting and design of large scale MPLS/RSVP networks. Joining Fortinet in 2018, initially supporting the UKI Carrier Service Provider but more recently BT from a sell-to perspective. Andrew has a varied background covering classical networking and cybersecurity which helps solidify the consolidated approach that Fortinet drives with Security Driven Networking.
Email: acrampton@fortinet.com
Making possible a digital world you can always trust
For over 20 years, Fortinet has been a driving force in the evolution of cybersecurity and the convergence of networking and security. Our network security solutions are the most deployed, most patented, and among the most validated in the industry. Our broad, complementary portfolio of cybersecurity solutions are built from the ground up with integration and automation in mind, enabling more efficient, self-healing operations and a rapid response to known and unknown threats.
Fortinet (NASDAQ: FTNT) has built its brand by securing the largest enterprise, service provider, and government organizations around the world. Fortinet empowers its customers with intelligent, seamless protection across the expanding attack surface and the power to take on ever-increasing performance requirements of the borderless network—today and into the future. Using the Fortinet Security Fabric architecture, Fortinet can deliver security without compromise to address the most critical security challenges, whether in networked, application, cloud, or mobile environments. Fortinet ranks number one in the most security appliances shipped worldwide, and more than 500,000 customers trust Fortinet to protect their businesses.
Learn more at https://www.fortinet.com, the Fortinet Blog, or FortiGuard Labs.
In this introduction we will focus on five key topics:
1. Fortinet Security Fabric – Cyber Security Mesh Architecture (CSMA)
2. Cloud and Multi-Cloud Security
3. Network & Security Convergence
4. Secure SD-WAN
5. Operational Technology (OT) Security
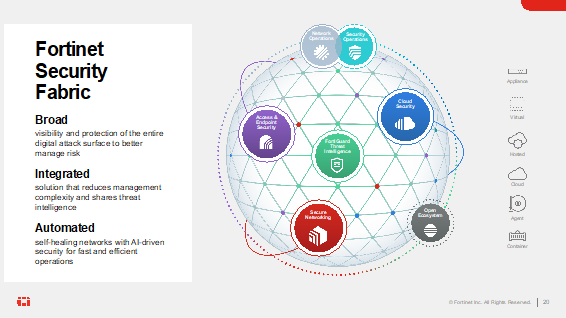
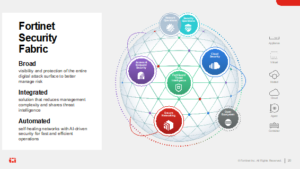
The Fortinet Security Fabric is at the heart of the Fortinet security strategy. It is a platform organically built around a common operating system and management framework to enable broad visibility, seamless integration and interoperability between critical security elements, and granular control and automation. The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
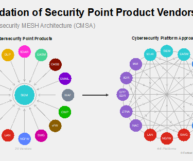
Cybersecurity Mesh Architecture (CSMA), coined by Gartner, is an architectural approach that promotes interoperability between distinct security products to achieve a more consolidated security posture. The Fortinet Security Fabric reduces operational complexity while ensuring compliance, emphasizes interoperability as well as analytics, intelligence, centralized management, and automation, and integrates with a broad ecosystem of technologies and vendors.
Today, nearly all organizations have adopted the cloud to modernize their operations, enable rapid innovation, and accelerate growth. The 2022 Cloud Security Report, a global survey of 823 cybersecurity professionals sponsored by Fortinet, reported that almost 40% of enterprises are running more than half of their workloads in the cloud. Moreover, that percentage is expected to increase to nearly 60% by 2024.
Many of these organizations have multiple disparate security solutions deployed, with few that integrate. And with each disparate cloud environment, management complexity increases as each one presents a siloed risk posture and limited remediation capabilities.
More than 90 percent of enterprises are adopting a multi-cloud strategy,1 and as they expand across multiple Infrastructure-as-a-Service (IaaS) cloud providers, their networking and security architectures must evolve. Specifically, enterprises are seeking a simplified and consistent way to connect their applications and workloads, improve the application experience for their users, streamline operations and costs with automation, increase their visibility into traffic patterns, and effectively apply consistent controls to reduce cybersecurity risks.
Here are three key requirements for networking and security when enterprises look to deploying applications across multiple IaaS clouds.
1. Common networking and security policy and enforcement framework for repeatable deployments.
One of the key challenges for multi-cloud deployments is that public cloud providers have different proprietary architectures built on frameworks, application programming interfaces (APIs), and toolsets specific to each one. The right multi-cloud solution provides a networking and security architecture that spans across these clouds, leverages the native features and functions of each cloud, abstracts that functionality with APIs, and then manages these connections dynamically using automation.
2. Application-aware networking for better user experience. Another important challenge with current networking technologies connecting multiple clouds is the underlying transport’s lack of awareness of different types of applications. It is important for the network to be application-aware to maximize the use of available resources, network conditions and capacity, control unimportant traffic, and understand end-user experience to deliver consistent performance for an organization’s critical applications.
3. Integrated networking and security architecture for effectiveness and efficiency. Multi-cloud deployments won’t reach their full performance potential if networking and security are separated. Each layer tends to use different technologies from different vendors. This causes gaps in coverage, which makes the deployment vulnerable to attacks. Central oversight, coordinated enforcement, and integrated communications between networking and security layers will close the gaps and reduce the potential for attacks significantly through intelligent deep packet inspection and segmentation of the network traffic flowing between applications and workloads across the multiple clouds.
Next-stage Considerations
There are fundamental differences in architecture between on-premises, hybrid cloud, and multi-cloud deployment models. Cloud infrastructure is largely API-driven, and it is designed for horizontal scaling (or scale-out) and rapid changes. In addition to that, it requires deep integration with underlying cloud platforms.
Security must be integrated with the network layer leveraging both cloud-native constructs (such as security groups) and advanced security such as intrusion prevention system (IPS), end-to-end high-performance encryption to protect network traffic, etc.
Enterprises adopting a multi-cloud approach can therefore benefit from a software-defined wide-area networking (SD-WAN) solution that provides a programmable, consistent, and cost-effective framework purpose-built for multi-cloud deployments
Conclusion
Fortinet helps secure the digital acceleration of cloud applications and workloads across all cloud environments. We do this by providing a friction-free, cloud-native solution that is integrated across major cloud platforms and security technologies alongside the Fortinet Security Fabric. Fortinet helps organizations maximize the value from their cloud-native security investments, as well as investments with the Fortinet Security Fabric to drive greater benefits in operationalizing cloud security. Together, these, along with FortiGuard Threat Intelligence, provide a comprehensive cloud-native security solution that reduces complexity, achieves greater visibility to protect your applications and workloads, and delivers capabilities such as consistent workflows that are enabled across all cloud environments to help you manage and reduce your risk.
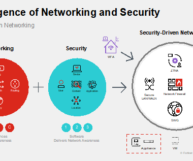
Traditional networking lacks awareness of content, applications, users, devices, location and more. Organizations have overlaid security solutions on to the network later to account for this shortcoming – but doing so has led to increased management complexity, performance bottlenecks, poor user experience, and the potential introduction of new exploitable gaps or vulnerabilities. A better Security-driven Networking approach converges networking and security into a single, accelerated solution. A specially designed operating system and security processors work in concert to greatly improve network performance and security posture, adding greater awareness while also improving user experience, easing management complexity, and decreasing footprint and power consumption.
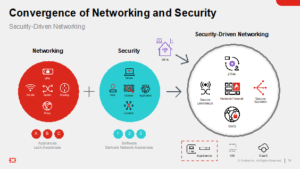
Fortinet’s Secure Networking approach integrates best-of-breed Security and SD-WAN with Secure SD-WAN solution delivering SD-WAN and security in one robust, easy-to-deploy, and easy-to-manage solution. Realizing the need for a full security stack for local Internet breakout traffic at the WAN edge, Fortinet began pioneering the concept of Secure SD-WAN in 2016. It is the only solution on the market which leverages proprietary custom SD-WAN ASIC hardware acceleration to supply best-of-breed next-generation firewall (NGFW) security, SD-WAN, advanced routing, and ZTNA application gateway capabilities - delivering a secure networking WAN edge transformation in a unified offering with unmatched scalability and performance.
Fortinet Secure SD-WAN powered by ‘Security-Driven Networking’ and purpose-built processors enables infrastructure and networking teams to deliver improved user experience, instant ROI, and simplified operations. Self-healing WAN capabilities, advanced routing, a natively integrated next-generation firewall, and centralized orchestration accelerate digital transformation at scale. Cloud services are more quickly accessed, and costs are often reduced by replacing MPLS lines with broadband. Further, zero-touch provisioning shortens deployment time. The solution enables future-proofing by consolidating LAN and WAN operations for SD-Branch, and is an ideal fit with emerging cloud-delivered SASE solutions.
The Fortinet Secure SD-WAN solution is chosen by over 20,000 global customers adding up to over 500,000 sites. Fortinet Secure SD-WAN has received multiple awards and “Recommended” ratings. In 2021, Fortinet received an AA rating from the CyberRatings SD-WAN test. Also, Fortinet is the only company listed in both Gartner Magic Quadrants for both Next Generation Firewall (Leader) and SD-WAN (Leader) for 2022 that uses the same platform, OS and management. In addition, Fortinet is ranked #1 in 3 of 5 use cases (Security-Sensitive WAN, Remote Worker, WAN for Small Branches) in the 2022 Gartner Critical Capabilities Report, two years in a row. One of the most recent and prominent ‘use cases’ highlighting the need for convergence of Networking and Security is SD-WAN, or Secure SD-WAN as coined by Fortinet.
In recent years, the Industrial Control Systems (ICS) upon which much of our critical infrastructure and manufacturing industry depends, have come under increasingly frequent and sophisticated cyber-attacks.
However, while the impact of a security breach on most IT systems is limited to financial loss, attacks on ICS have the added potential to destroy equipment, threaten national security, and even endanger human life. With this critical distinction also comes a troubling difference in the profiles and motivations of potential attackers. While the lion’s share of modern cybercrime is motivated by financial reward, ICS have recently become attractive targets for terrorism and cyber-warfare.
Previously air-gapped OT environments are becoming increasingly connected due to Digital
Transformation initiatives and a growing need to support distant assets remotely. The fundamental assumption- a discrete OT network - is undermined by this increased connectivity. The Fortinet Security Fabric provides a broad, integrated, and automated platform addressing the challenges of IT-OT convergence and tailored to the constraints found in OT and IT. Solutions
to convergence challenges include customizing products to unique OT environmental conditions, such as rugged firewalls and switches, advanced threat protection offerings including endpoint protection, deception, sandboxing, and SOC/NOC tools that can synergistically scale across IT and OT.
* refer to download section for more information*
Other useful videos:
Sorry no gallery at the moment!
